Flexible Security Testing for Today’s Threats
According to a recent Enterprise Strategy Group survey, at least 75% of large enterprises are considering a shift to next-generation, platform-based security testing solutions. Increasingly dynamic modern applications, growing attack surfaces and AI-enabled cyberthreats have led many organizations to reassess traditional methods of pentesting.
Synack applies a diverse range of testing methodologies for the modern era, earning the trust of Fortune 500 companies and mission-critical government agencies. Whether you want to achieve Payment Card Industry (PCI) compliance, prepare for the next Log4j or run tests on your AI/LLM models, we have you covered.
The Premier Penetration Testing as a Service Platform
On-Demand, Diverse Talent & Testing
The platform grants rapid access to a curated community of over 1,500 security researchers, offering a wide range of testing expertise and high-quality outcomes. Break free from the limitations of a small, unchanging pool of pentesters.
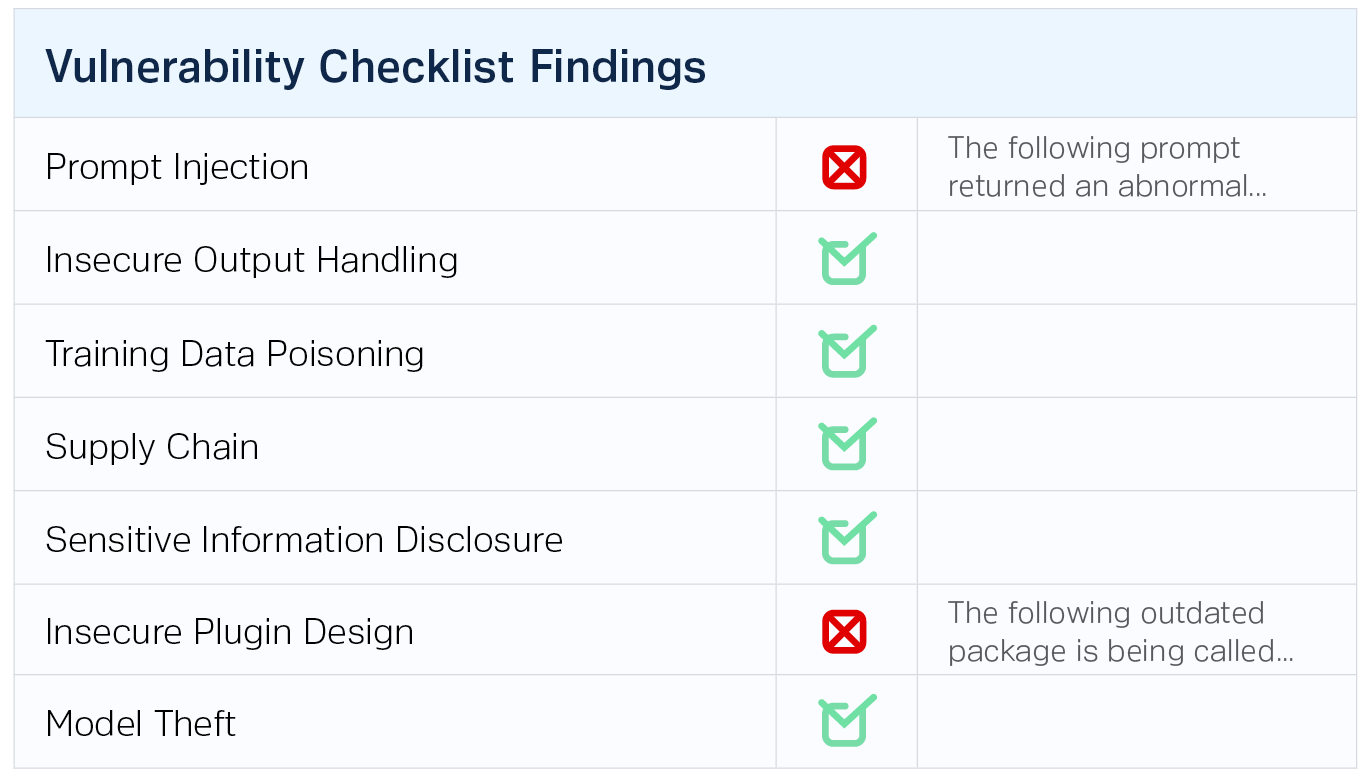
Essential Reporting in One Platform
No more unwieldy PDF reports: Findings are archived and searchable within the platform, ensuring easy access for a range of security team members and systems.
Comprehensive Security Testing Offerings
Synack can check the box on all offensive security testing requirements, from red team operations to zero-day response. We provide a high degree of flexibility and can meet you where you are.
Structured Testing for Specific Assets