In an ideal world, you find critical vulnerabilities through your security testing program and developers patch them to improve your attack surface’s posture.
In the real world, while you may find the vulnerabilities, getting your developers to understand the results of your testing and patch those found in the code may prove difficult. According to Comparitech, the average remediation time of a vulnerability is around 58 days. A report by Synopsys points to continued prevalence of Lo4j vulnerabilities (present in 11% of reviewed codebases) as evidence of organizations failing to implement patches.
Why do organizations struggle to get known vulnerabilities patched?
Us vs. Them Mentality: Understand Your Developers
People don’t like being told what to do, at least without a good reason. Imagine if someone came to your home periodically and criticized your furniture choices, your cooking, your wardrobe and offered you suggestions for improvement. From a developer’s point of view, this is exactly what is happening with security testing. Pentesters are finding flaws in their work, and the security team is delivering the results with expectations for correction, perhaps lacking some bedside manner.
On top of that, hiring teams on both the developer and security side are drowning in the number of skills required to be successful. StackOverflow’s 2022 survey identifies over 40 scripting/programming languages today’s developers are required to work with or learn, and Fortinet’s 2023 Skills Gap report details that 68% of organizations face cyber risk because of cybersecurity skills shortages.
Involve Your Developer Teams From the Start
One way to improve the likelihood of developers responding positively to security testing results is to involve them from the beginning. Give your developer teams opportunities to give feedback on vendors you are considering for security testing, make sure they know how the results will be delivered, and reassure them that quality results that need their attention will be delivered based on how skilled the researchers are doing the testing.
If there’s a platform with features that would benefit them directly, show them a demo and assure they’ll have login access to interact with the tool directly to give them a sense of ownership.
By involving them early and often, developers can expect to receive the results from a testing program they helped vet and approve. However, that brings us to our next point.
The Security Testing Program Has to Work
Traditional pentesting often involves a couple of researchers looking for vulnerabilities once a year and summarizing their findings in a static PDF. The thick PDF gets passed over to development teams and can often look like an overwhelming list of findings. Additionally, some findings may only be noise, deemed not of high enough impact to fix. If developers later have questions about the valid findings, there’s no easy way for them to communicate with the researcher who found it to help replicate the vulnerability.
Enter modern Pentesting-as-a-Service (PTaaS) solutions. These modern pentesting programs can offer appealing benefits to researchers that make consumption of findings easier and remediation faster and more effective.
The Synack Platform is one such solution that offers:
- Delivery of vulnerabilities in real-time, rather than all vulnerabilities at once
- Triaged findings, so developers only see high quality results
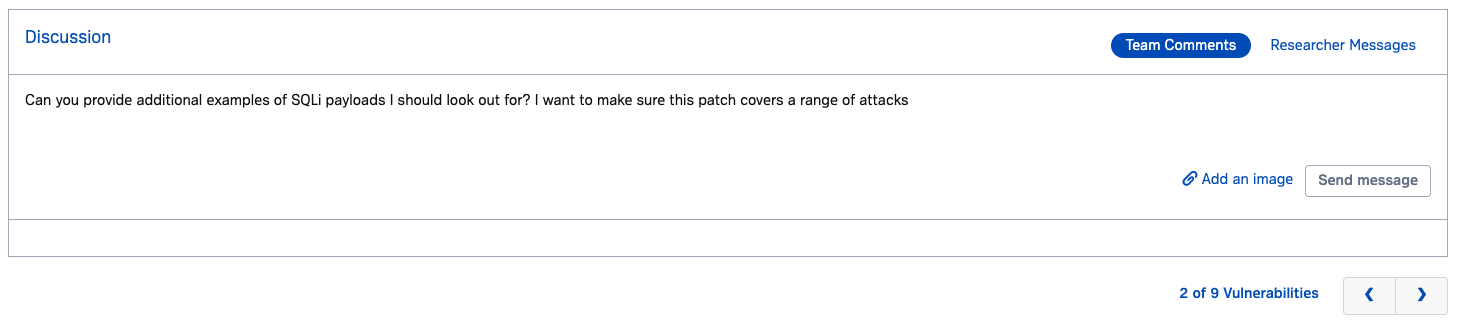
- Rich information on findings like screenshots and suggested fixes
- Commenting back and forth with the researcher who found the vulnerability
- On-demand patch verification to prove successful remediation
- Reports on patch efficacy over time
- Role-based access control (RBAC) for controlled user groups with as-needed access
- Integrations with tools like Jira, ServiceNow and Microsoft Azure DevOps
Remediating Vulnerability Findings with Developer Buy-in
Spinning up a pentest without involving the developers and then expecting them to act on the findings is not a recipe for success. Rather, involving them in the selection of a pentesting program and setting clear expectations for the delivery of findings will ensure better cooperation and results.
That means the testing program you choose will have features that benefit developers’ workflows, such as real-time delivery of findings through a platform, ability to communicate with researchers on findings and fixes, and integrations with existing tools.
If you’re looking for a program with benefits that developers will embrace, reach out to Synack today.




